If you want the best privacy protection as well as great ad tracking prevention on iOS, VPNs are your best bet, although without some caveats.
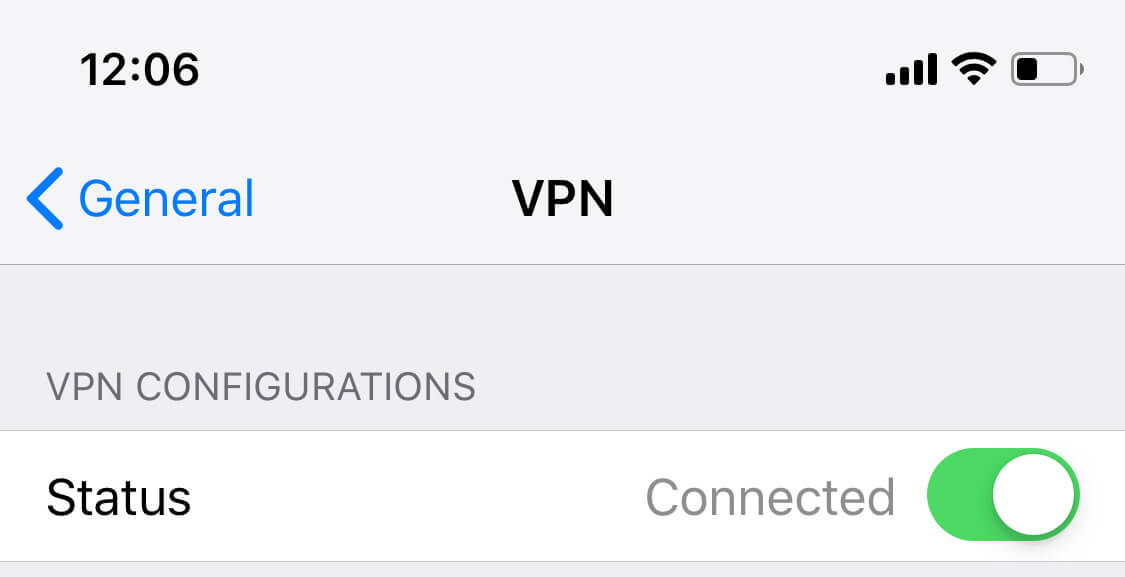
First off, let's start with what a VPN means. VPN is a Virtual Private Network which means connecting your remote devices into a single private but virtual network since the devices may not actually be connected directly to each other.
Usually when your device makes a connection to any service, the data you're sending and retrieving travels through dozens of nodes until it reaches the server on the other end. And you can't be sure none of the nodes in between aren't compromised and for example aren't storing your data without your consent. The main advantage of using VPNs is that all of your Internet traffic travels encrypted and is available only to you and the server and no one in between. Of course it's not a bullet-proof solution but it's the best and easiest way to make your data as much unusable as possible to non authorized middleman parties. Especially if you're controlling your VPN, since paid or public VPNs which provide transparency and security might not actually do it and do the exact opposite - log all of your data for their own benefit.
For most of the people, and even for advanced users using a VPN might be overwhelming and hard, especially if you decided to set it up yourself and not to use a public one. And without specific knowledge such setup may be leaking your data even more than no VPN at all. But the manuals like this cover the security basics quite well, as well as some of the public VPN providers hold many years of trust without being revealed in scandals of (un)intentional data leaks.
So using a VPN generally is a good idea - you get your traffic encrypted which keeps your private data safe and as a side effect you get even some ad tracking prevention since even your basic data stops being available to the advertisers who keep their trackers on many websites and services you visit. And if you're using your device to access sensitive data by using public wifi or in countries with regulated Internet access - VPNs are a must for you. Also if you want to access country specific/restricted resources, there is not much choice except using a VPN at all, which in this case would make you have an external IP address that belongs to that country and you will appear like you're browsing from within that region - that's another advantage of using VPNs.
If you plan on using VPNs, secure the most important devices first. But if you can - use VPNs on all of your devices. I tried going this route, but here are some downsides that made me stop using them:
- Using VPNs on any of the device will make the Internet feel slower. The reason for it is that instead of your packets going directly to the server you're trying to reach they go a longer route through your secure server first, and that adds up delay to each of your web request and as a result everything loads noticeably slower.
- Also your max speeds might take a hit. With my 250/20 Mbit speeds at home I was getting about 20/10 Mbit using a public VPN since they are often sharing their channels within many users. Setting up your own VPN somewhere with high speed Internet access should make it better, but the delays mentioned before still won't improve much and will also cripple your speeds.
- The speed hit affects mobile devices connected via cellular the most since those already have a pretty high delay of transferring data through the air. So on mobile the speed slowdown is noticeable the most.
- The other problem (at least with iOS) is that the device might disconnect from the VPN in the background and leave portions of your background traffic unsecured as well as some traffic before it reconnects after unlocking the phone. From what I understand the VPN disconnects to preserve battery which it uses 10-15% more of than without having an active VPN connection - this in my opinion is also a significant problem with VPNs on the go.
That said, if you need your connections to be secure and untraceable - you still have the option even though it would cost you Internet speed and some battery life, but if you need it in certain circumstations, that's a fair tradeoff.
In my tests I was using Tunnelbear (loved its cuteness and service, until it was purchased with a not very trust McAffee recently), SurfEasy and my new favorite PIA because of their high long standing reputation. And you should care about the reputation of the company that keeps your traffic private 🙂 As for setting up your own VPN - I used DigitalOcean's manual from the link above but with Ubuntu 16.04 instead of 18.04.
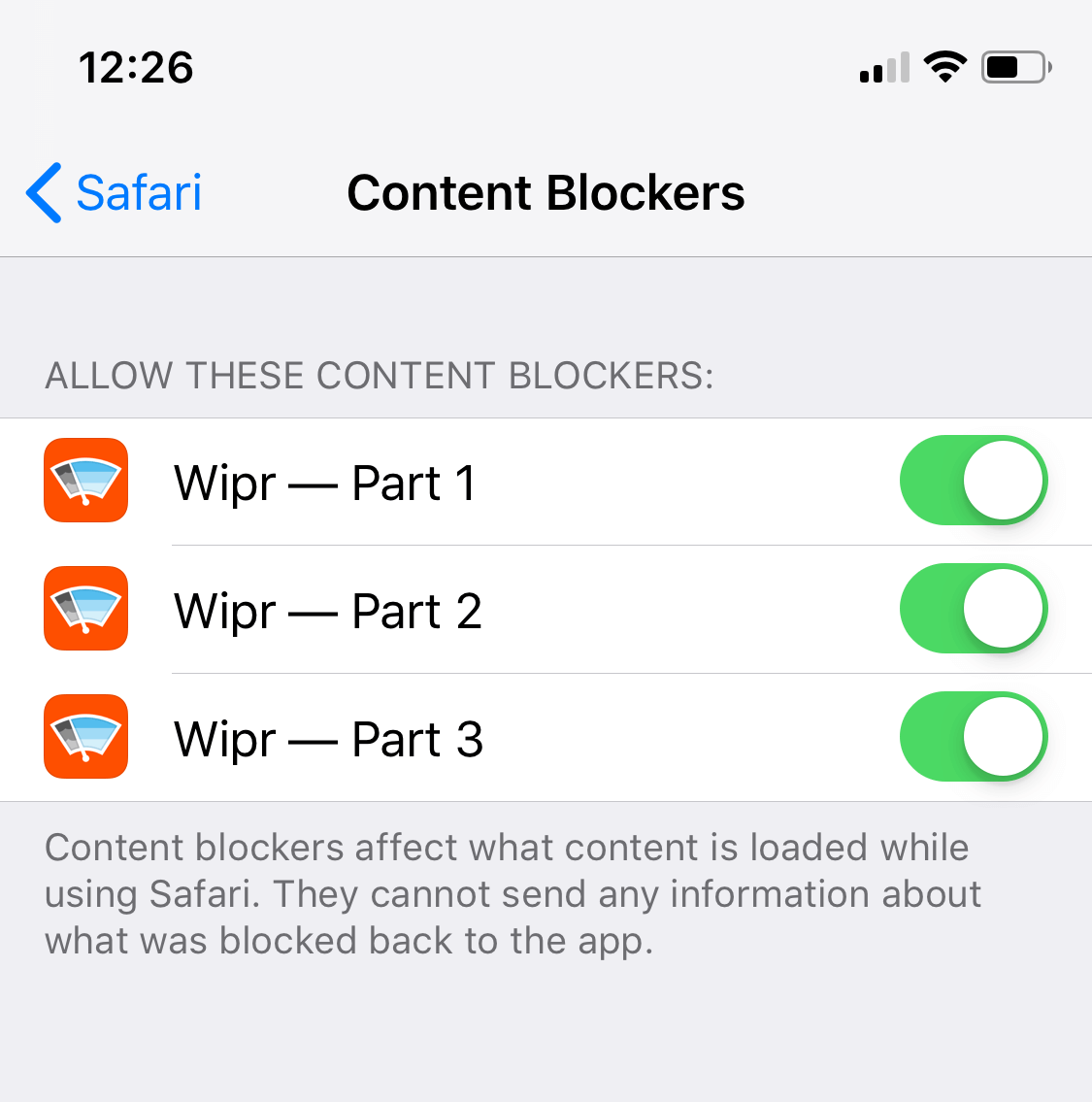
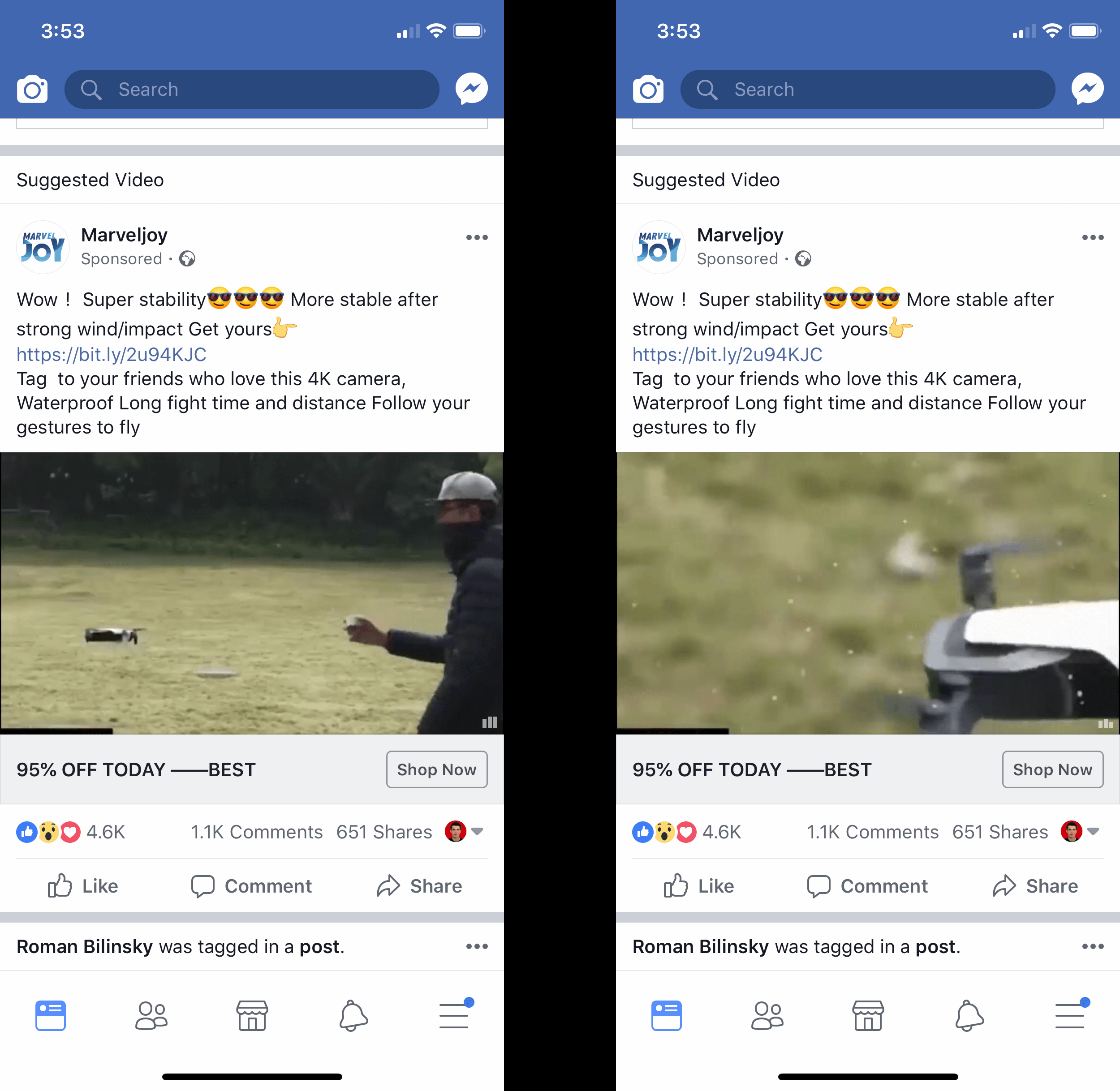
If you don't need that level of security and just want to browse the Internet without ads, here's my breakdown on the best iOS and Android adblockers as well as a post on what privacy concerns you should consider while using and adblocker in the first place.
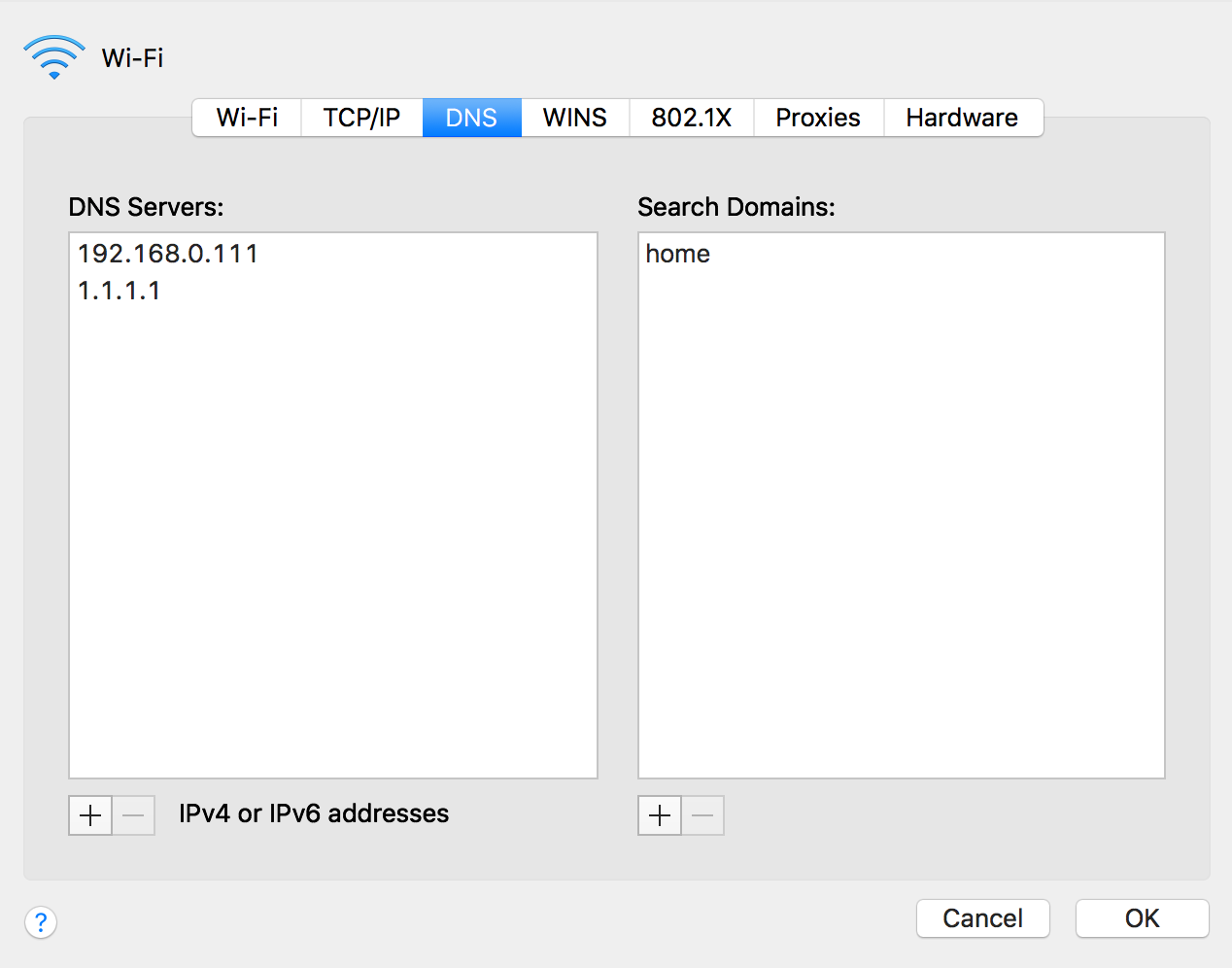
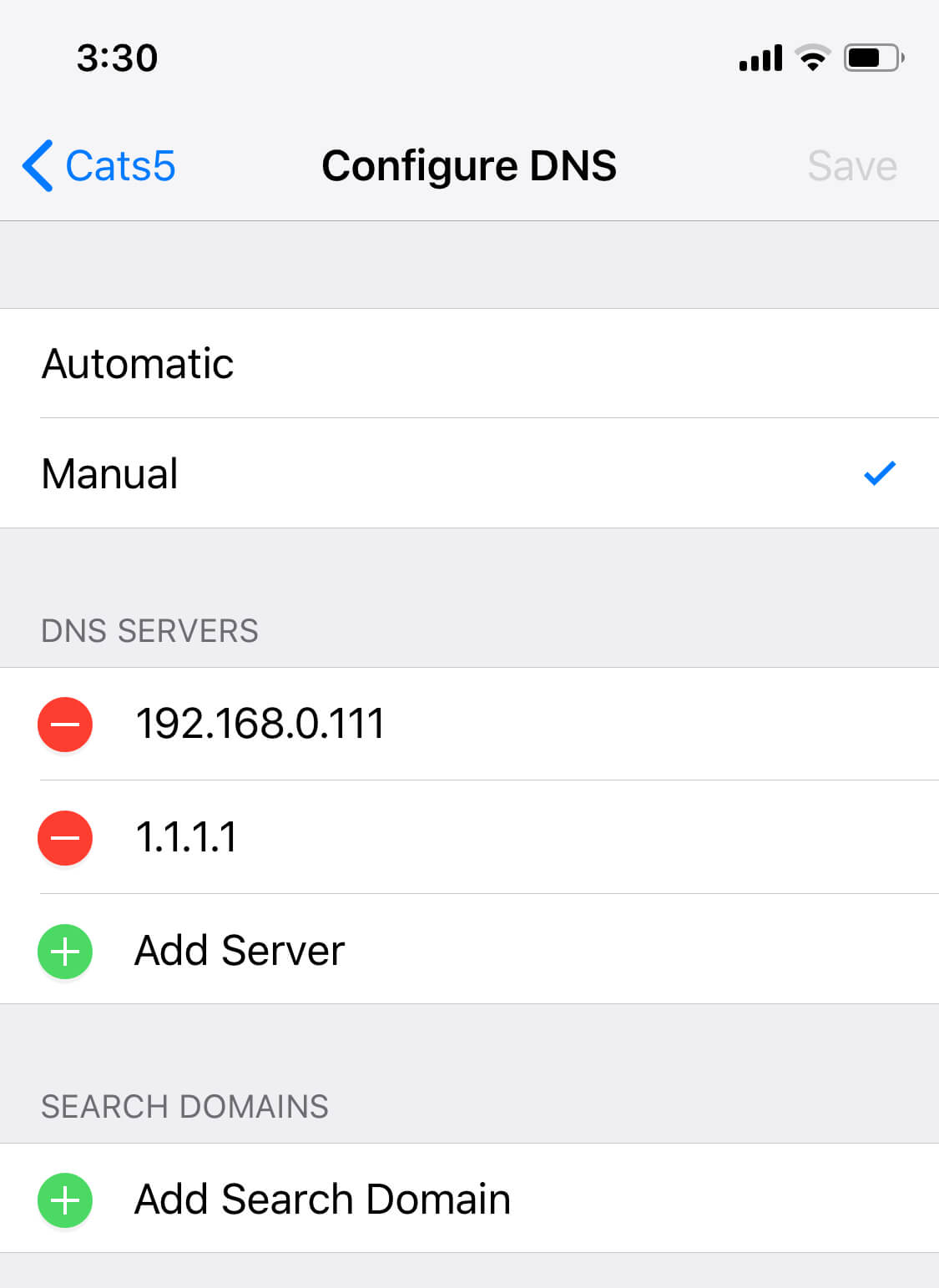
But if you want something better for filtering ads outside of Mobile Safari on iOS and on other devices, you can switch your DNS server on them to have better filtration all the time without any penalty on the battery. And if you want to have custom DNS servers for your iOS device not only in your local Wi-Fi area, you can setup DNSCrypt and have ads filtering on the DNS level everywhere you go!